The previous article of this series goes over the basics of Authentication Attacks and Indicators that your account could be at risk.
You might not be aware that authentication attacks are increasing in volume in the threat landscape. What’s worse is that the source of these attacks are changing in such a way that it is difficult to block these networks without having a negative affect on normal traffic and connections. This article will go over the different types of authentication attacks and good password practices that can mitigate the risk from these attacks.
Brute Force Attacks
Brute force authentication attacks are the most common type that people are aware of. This technique attempts to crack passwords by trying every possible combination of letters, numbers, and symbols. Brute force attacks are less effective against accounts from online services because these services usually have mechanisms to prevent a high volume of password attempts over a small period of time. Where this technique shines is offline. For example, trying to crack the password of a password protected file, or the password of a device such as a laptop. Without mechanisms in place to stop a high volume of password attempts, it is only a matter of time before a weak password is cracked.
Defense against Brute Force Attacks
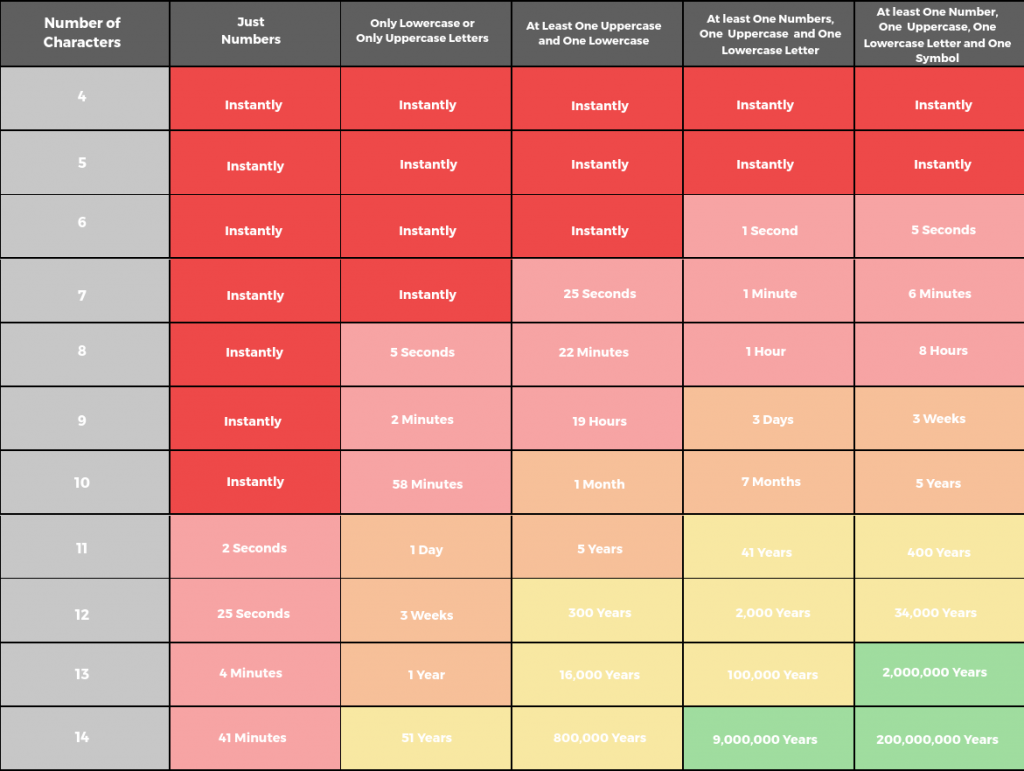
Against brute force attacks, the strongest password is a long password. A strong password also has at least one lower case, upper case, number, and symbol. A strong 6 character password can be cracked in 5 seconds, 8 characters cracked in 8 hours, and 12 characters cracked in 34,000 years. As you can see, the number of characters exponentially boosts the defense against brute force techniques.
Dictionary Attacks
Dictionary attacks are another common type of authentication attack. Don’t be fooled by the name, a ‘dictionary’ attack is not literally using a dictionary; it refers to any list of passwords. Instead of attempting every possible combination, a prepared list of words are used to increase the chances of cracking passwords. If you search for the most common passwords, you can be sure that any password on those lists will be cracked instantly.
Defense against Dictionary Attacks
Do not use a password that is a single dictionary word, and make sure your password is not on a list of the most common passwords. No, you are not clever for having ‘q1w2e3r4t5’ as your password.

Password Spraying Attacks
Password spraying attacks are a refined version of dictionary attacks. A common security measure on most systems is limiting the number of times a password can be entered for a particular account within a certain time frame. Password spraying avoids getting ‘locked out’ by attempting a limited number of passwords across multiple accounts, thus avoiding alerts and suspicion. For example, this attack could attempt 3 different passwords across 100 different accounts of a particular service (your account being one of them).
Defense against Password Spraying Attacks
Since the passwords used in this attack are similar to dictionary attacks, not having a dictionary word as a password is also a defense. Having an uncommon username also helps. Sometimes password spraying attacks will use a list of known usernames for the service it is attacking, and other times it will use a dictionary list of common usernames. A username like ‘john’ would be attacked more often than ‘a_john_250’ in the latter case.
Credential Stuffing Attacks
Last, but definitely not least, are credential stuffing attacks. These attacks utilize lists of real username and password combinations. These lists come from the growing number of data breaches, some of which contain legitimate username and password credentials. Credential stuffing attacks leverage this data and will break into accounts that have not updated their passwords after a data breach. They will also attempt these username and password combinations across all services to exploit the fact that some people use the same username and password for multiple accounts.
Defense against Credential Stuffing Attacks
You can check if your account has ever been a part of a data breach at haveibeenpwned. If it has, immediately update your password if you haven’t already. Also, do not use the same username and password across different services. This might seem like an easy trick to reduce the need to memorize your credentials, but it is one that drastically reduces the effectiveness of your security.
Summary of Good Password Practices

At the end of the day, we are humans and have a finite ability to remember passwords. Above all, the best password is one that you can remember; it just also has to have all the other traits of a strong password. If you’re forced to write down your password on a sticky note on your monitor, you’re just creating another failure point.
- 8-12 characters is normally the recommended length, but you already know the immense difference between an 8 character and 12 character password. Stick to a minimum of 12, and don’t forget to at least have one upper, lower, digit, and symbol.
- Have a password that you can remember so you don’t have to write it down elsewhere.
- If you must use ‘dictionary’ words (as they are easy to remember), use at least 3-4. Even better, you can utilize the first letter of an easy to remember quote/phrase as your password. For example: Tim$IpTyCG!! (this is my super incredible password that you can’t guess!!).
- Do not use the same username and password across different services.
- Do not use a password that exists in any ‘common passwords’ list.