In last week’s article we covered Freenom domains and how they are used in Digital Ocean snowshoe spam campaigns. Let’s see what kind of activity has been coming from Digital Ocean over the past week. While not a Freenom TLD, this time we’ve also included .xyz domains in the data set for those researchers who have expressed interest.
Aug14 134.122.24.207 x2 rdns0.ressua.xyz 206.189.198.236 x2 mail.thebehringtools.xyz 46.101.237.35 x1 box.cmail.xyz Aug15 161.35.116.178 x1 marketpress.xyz 161.35.53.168 x2 buntydeals.xyz Aug17 128.199.77.21 x1 mx13.camouflage84259.xyz 142.93.213.48 x5 xv20.zazomika.cf 161.35.120.116 x1 mail.marketvaluerates.xyz 164.90.159.129 x10 box.canopusvietnam.xyz 206.189.128.113 x28 xv20.524.pinotvineryms.cf 206.189.178.128 x1 rdns0.pertsd.xyz Aug18 134.209.153.18 x11 swn0.pinotvineryms.ga 142.93.193.164 x11 rdns0.unnsa.xyz 142.93.219.160 x2 srv0.bulkemails123.tk 161.35.226.60 x14 box.alphadaero.xyz 161.35.73.103 x2 swn0.pinotvineryms.ml 178.62.220.63 x1 box.bufferty.xyz 206.189.204.51 x2 designopro.xyz 206.189.228.86 x2 rdns0.proods.xyz 68.183.67.246 x2 swn0.zazomika.ga Aug19 128.199.233.131 x1 mailer.strongf.xyz 159.89.232.82 x3 rdns0.hyunn.xyz Aug20 139.59.20.28 x2 iux0.strinoemenker.tk 157.230.24.67 x36 iux0.miditruni.cf 161.35.98.28 x5 rdns0.iggds.xyz
So, what more can be said about this activity other than it is garbage, easily preventable, and (disappointingly) not being dealt with? Let’s dig deeper and check out what kind of spam is being sent.
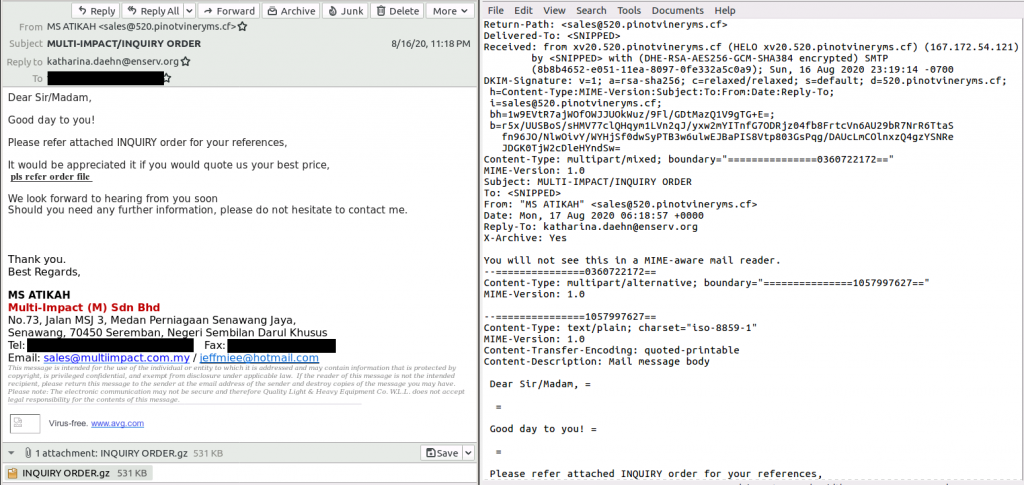
The above case is purely a malicious email, pretending to be an interested buyer and trying to get you to download and execute the attached file. This attached file is identified as the malware ‘AgentTesla’, a keylogger and RAT (Remote Access Trojan) with the ability to exfiltrate data into the hands of a bad actor.
You might think it is quite obviously spam, and that you’d never fall for it. However, sometimes that is the point. Spammers find success targeting the most gullible people, the ‘low hanging fruit’ if you will. It’s frustrating that large providers allow their networks to be abused like this, with no repercussions to their lack of action.
Whom does the onus belong to when it comes to malicious activity occurring? Should the end users, the victims that this spam targets, simply educate themselves and purchase better anti-spam and anti-malware tools? Should we wait for the Spammers to discover the error of their ways and turn to a new light? Or should the network providers, the ones that can most easily detect and deal with the problem, be responsible for their non-efforts when it comes to cleaning up the obvious abuse of their services?
Sure, reporting to abuse contacts is good when it works, but too much of the time it is ‘bandage’ fixes and not systematic changes to prevent future abuse. As mentioned, we’ve been seeing this pattern for years, and it isn’t stopping. Malware, phishing, and spammy marketing continue to pour out of this network.